Control modbus with UDP protocol
The User Datagram Protocol (UDP) is one of the core members of the Internet protocol suite. Applications that do not require reliable data stream service may use the User Datagram Protocol. It provides a connectionless datagram service that emphasizes reduced latency over reliability.
UDP is a connectionless and unreliable transport protocol. The two ports serve to identify the end points within the source and destination machines (Figure 1). User Datagram Protocol is used, in place of TCP, when a reliable delivery is not required. However, UDP is never used to send important data such as web-pages, database information, etc. It has no handshaking dialogues. Streaming media such as video, audio and others use UDP because it offers speed. Losing a small package of data can be unnoticeable.
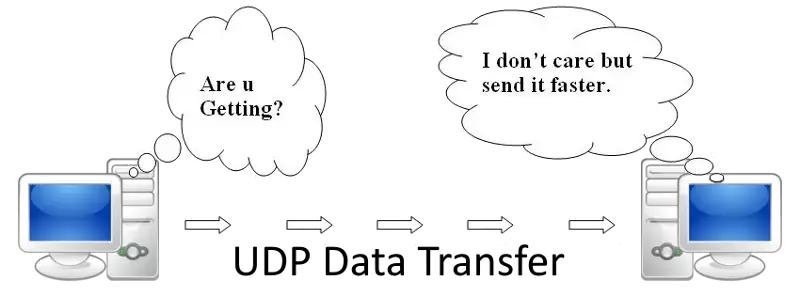
UDP provides a connectionless and unreliable transport service since it does not issue acknowledgments to the sender upon receipt of data nor does it inform the sender that a data package was lost. Data integrity can suffer by dropped packets, mis-sequenced packets or by the receipt of duplicate packets. Any of these situations can occur without the knowledge of the sender, so the sender continues to send UDP packages.
It appears that UDP is no better than the IP protocol but there is one big difference. UDP introduces the concept of port numbers, which are used by the application layer that resides above UDP (table 1). Port numbers have significance in terms of actions requested by the application itself that require a particular response by the receiving station.
| OSI Layers | Protocol data unit (PDU) | Function |
| Application | Data | High-level APIs, including resource sharing, remote file access |
| Presentation | Data | Translation of data between a networking service and an application including character encoding, data compression and encryption/decryption |
| Session | Data | Managing communication sessions i.e. continuous exchange of information in the form of multiple back-and-forth transmissions between two nodes |
| Transport (TCP, UDP) | Segment (TCP) / Datagram (UDP) | Reliable transmission of data segments between points on a network including segmentation, acknowledgement and multiplexing |
| Network (IP) | Packet | Structuring and managing a multi-node network including addressing, routing and traffic control |
| Data Link | Frame | Reliable transmission of data frames between two nodes connected by a physical layer |
| Physical | Bit | Transmission and reception of raw bit streams over a physical medium |
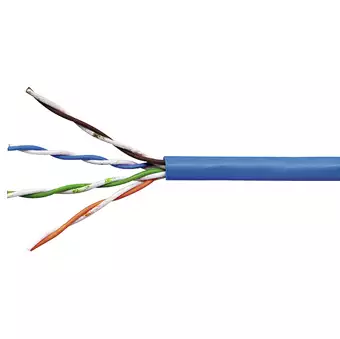
Unshielded twisted pair (UTP) are mostly used in the physical layer. A typical subset of these colors (white/blue, blue/white, white/orange, orange/white) shows up in most UTP cables (Figure 2-3). The cables are typically made with copper wires measured at 22 or 24 American Wire Gauge (AWG), with the colored insulation typically made from an insulator such as polyethylene or FEP and the total package covered in a polyethylene jacket.
UTP uses twisted wire pairs. Twisted pair cabling is a type of wiring in which two conductors of a single circuit are twisted together for the purposes of improving electromagnetic compatibility. Twisted pair cabling is often used in data networks for short and medium length connections because of its relatively lower costs compared to optical fiber and coaxial cable.
|
|
|
Wi-Fi is another physical layer type. It works on the basis of IEEE 802.11 Standard. The protocol architecture consists of Physical Layer with two sublayers PLCP & PMD and Data Link Layer consists of MAC and LLC sublayer. The Wi-Fi network consist of a Wi-Fi client, access point and LAN. LAN may consist of Ethernet Switch, RADIUS Authentication Server etc.
Basically Wi-Fi works in half-duplex mode and Wi-Fi standard consist of only Physical Layer and Data Link Layer. Other layers are similar to TCP/IP model or OSI model in other applications.
The physical layer can transfer both TCP or UDP packages, although this page describes UDP only, so let's continue by examining the UDP package header. You will also see how an UDP package is transferred between two stations (e.g. computer).
UDP header
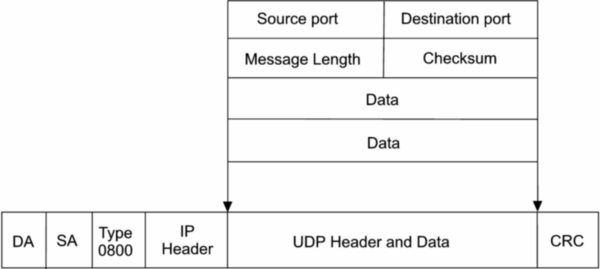
Because UDP is significantly more limited in capability than TCP, its headers are much smaller (Figure 2). A UDP header contains 8 bytes, divided into the following four required fields:
- Source port number (2 bytes): This is a port number used by the source host (range: 0 to 65,535).
- Destination port number (2 bytes): This is a port number used by Destination host (range: 0 to 65,535).
Source and destination UDP port numbers are the communication endpoints for sending and receiving devices. - Message length (2 bytes):
The length field in UDP represents the total size of each datagram including both header and data. This field ranges in value from a minimum of 8 bytes (the required header size) to sizes above 65,000 bytes. - UDP checksum (2 bytes):
Similar to TCP, a UDP checksum allows receivers to cross-check incoming data for any corrupted bits of the message.
Source and destination ports are each 16-bits long and, therefore, require four bytes. The message length of 16-bits indicates the length of the header and attached data. A 16-bit checksum is used to check the validity of the header and data. The UDP header and attached data, which comes from the application layer, are encapsulated into the IP data field. An IP header, which provides station addressing, precedes the UDP datagram and the complete IP datagram is encapsulated into the frame of the data link layer technology used, such as Ethernet, and sent to the desired station where the complete process is reversed. Notice that the only contribution UDP provided was the assignment of port numbers for use by the application layer. If UDP is to be used, the application layer must worry about acknowledging message receipt, correctly ordering received packets into meaningful messages, discarding duplicate packets and requesting retransmission of faulty packets since UDP does not provide this service. However, if the application layer was originally designed to provide this reliability of service, there is no reason to have the transport layer duplicate effort so UDP makes sense. UDP has low overhead and executes quickly, making it attractive for control networks.
Well-known UDP/IP port numbers
This is a list of UDP port numbers used by protocols of the transport layer of the Internet protocol suite for the establishment of host-to-host connectivity. Port numbers are assigned in various ways, based on three ranges: System Ports (0-1023), User Ports (1024-49151), and the Dynamic and/or Private Ports (49152-65535). The most well-known UDP ports can be found in table 2. To find the full list of port numbers, please click here.
| Port number | Application Protocols |
| 20 | FTP-DATA File Transfer Protocol data (transfer) |
| 21 | FTP File Transfer Protocol control (command) |
| 23 | TELNET Telnet |
| 25 | SMTP Simple Mail Transfer Protocol |
| 37 | TIME Time |
| 69 | TFTP Trivial File Transfer |
| 79 | FINGER Finger |
| 110 | POP3 Post Office version 3 (POP3) |
| 123 | NTP Network Time Protocol |
| 143 | IMAP2 Internet Message Access Protocol v2 |
| 161 | SNMP Simple Network Management Protocol |
Summary
UDP can be quite effective if the application layer can handle error checking and retransmission. If the goal is fast, although unreliable flow of data, like a video stream or voice call, UDP is the best choice. Both TCP and UDP application protocols use port numbers (find all ports here) and when used with IP addresses create unique socket definitions across the network. These socket definitions facilitate the processes between the stations on the control network.
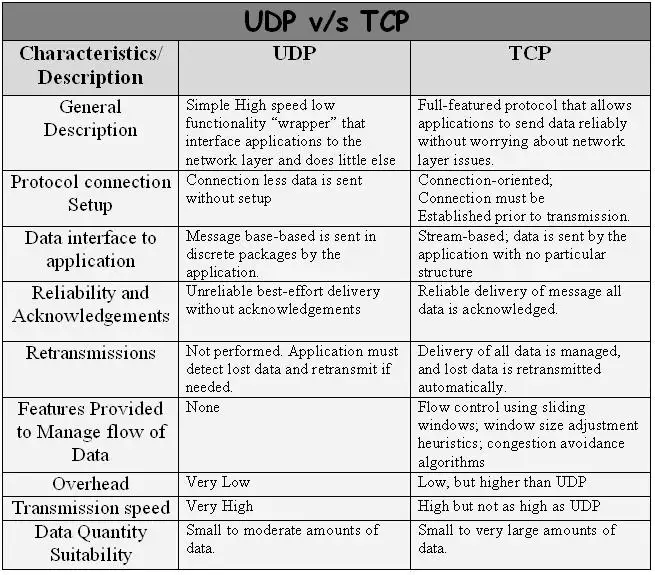
As a summary read about the most significant differences of the two IP protocols (Figure 6). TCP is more reliable although slower. UDP is faster, but less reliable, since there is no data acknowledgement in UDP and it has no connection setup handshake, while TCP has. This guarantees the speed of the UDP. Thanks to data acknowledgement TCP repeats false messages. This means it can transfer large amount of data reliably.
Contents retrieved from
- http://www.industrialethernetu.com
- https://en.wikibooks.org/wiki/Communication_Networks/TCP_and_UDP_Protocols